How is the security of WordPress? Not particularly well, because it comes with a number of serious vulnerabilities. And because more than 40 percent of the Internet currently runs on WordPress, it's a popular target for attack. The good news: The most important vulnerabilities can be easily eliminated.
The beauty of WordPress is that really everyone can use it. Actually, you only need an internet connection and you can get started. The security of WordPress is quite different. Perhaps because of the ease of use not all deal with how secure WordPress actually is by design.
In any case, because of its great strengths - the incredible range of functions and the diverse designs - WordPress tends to be very insecure. The modular structure offers massive points of attack. And these are of course also exploited by hackers. And automated, around the clock, 365 days a year.
But don't worry: These built-in weaknesses of WordPress can be eliminated very easily. And first of all completely without any additional security plugin.
Of course, I don't want to talk you out of your security plugin. It may even be very useful. But securing your WordPress website is not finished with its installation. And before you get into shadowboxing fights with pseudo threats, it makes more sense to compensate for the basic weaknesses of WordPress.
In detail, today's topic is:
- the admin area and why it is so vulnerable
- the weaknesses of the modular structure of WordPress
- the role of WordPress hosting in the basic security of your website
"But my website is not interesting enough"
Make no mistake: this assumption is simply wrong. Every WordPress website is valuable as an attack target. For example, as a spam spinner, part of a botnet, or advertising platform for phishing websites.
And in case of doubt, it doesn't matter how small, new or little visited your website is. Because in the end, you and your business are the ones who suffer. Your newsletter may be classified as spam, users may be warned against visiting your website, and your Google ranking may suffer because your website is blacklisted.
What I'm saying is that simply because of the popularity and proliferation of WordPress, WordPress websites are a grateful target for attack. And that's regardless of their content and purpose.
"*" indicates required fields
The WP admin area is particularly vulnerable
The login page is accessible via the suffix "wp-admin" by default. That's why it's also a very frequent target of attacks - especially so-called brute force attacks. These attacks are among the most common hacks against WordPress websites, because they are easy to automate. A brute force attack tries to guess the right combination of name and password. So if the password is weak or the login area is not protected, a brute force attack can either succeed and someone else can successfully log into your WordPress, or the massive amount of login attempts can cripple your website.
Wordfencethe well-known manufacturer of the security plugin of the same name, recorded an average of 34 million brute force attacks in March 2017 alone - on a daily basis. In comparison, the so-called "complex attacks", i.e. exploiting specific security vulnerabilities, are at a level of 3.8 million attacks daily.
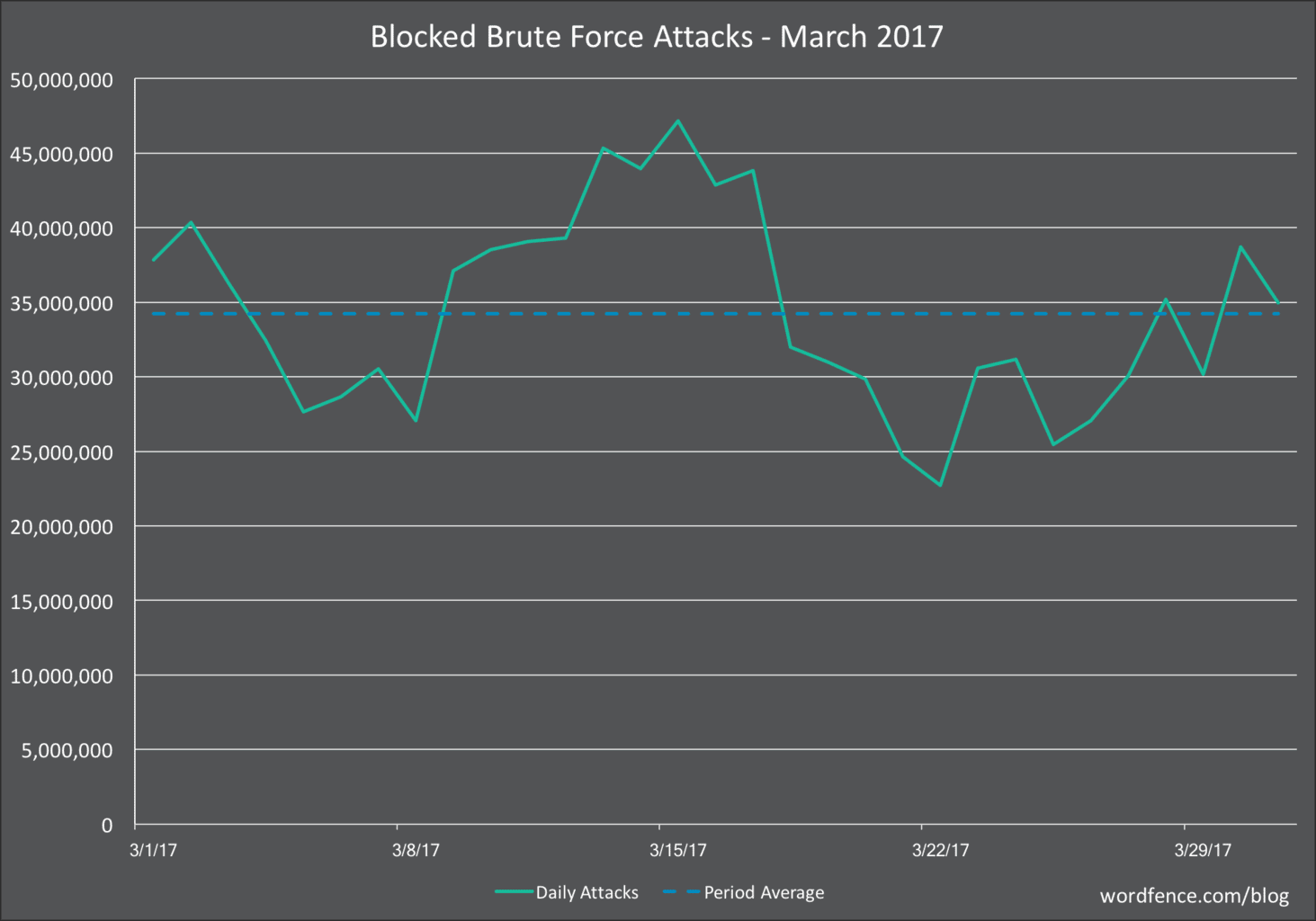
However, since Wordfence only counts attacks that were repelled by its own software, the number of unreported cases is even higher.
But the good news is: Although the attack on the WP admin area is very easy and can be automated quickly, the protective measures against it are very simple. To secure your WP admin area, you can put up protective walls in three places:
- At the WordPress level, through strong passwords
- At the login itself, by limiting the number of login attempts
- Before login, through a blacklist
1) The old chestnut: strong passwords
Brute force attacks are very mindless attacks. In principle, they only guess. Therefore, a strong password can actually be enough to make the attacks fail. So let's make it short: the strong password is mandatory. This includes: Letters, numbers, special characters and upper and lower case letters. And of course, two-factor authentication is also a good idea.
TIP: With password managers, it is not only easy to create secure passwords, but also to manage them. Apple computers, for example, offer a convenient way to manage your passwords offline with the program "Schlüsselbundverwaltung". You only have to remember one master password (which should be as complex as possible, of course). Cloud-based password management programs such as 1Password, LastPass or X-Key Pass work in the same way.
2) Limit the number of logins
You can see it impressively in the numbers from Wordfence : Brute force attacks are the most common attacks on WordPress websites. So the probability that your website becomes a victim of such an attack is very high. And so that the high number of login attempts does not burden your website unnecessarily, there is the possibility to limit them.
An IP is then blocked for a certain time after three failed attempts, for example. If the IP then reaches the limit again, the blocking period increases successively. In this way, you very quickly limit the number of possible attempts to such an extent that the attack becomes useless.
Depending on how low the blocking threshold is set, this method can also protect against an attack with changing IPs. The easiest way to protect your login area is to use plugins. There are for example WP Limit Login Attempts, Login Lockdown or one of the big security plugins like Sucuri, Wordfence or All in One WP Security. The websites hosted at Raidboxes are already equipped with brute force protection on the server side. So an additional plugin is not necessary here.
3) Blacklisting
At security companies like Sucuri or Wordfence , a large part of the working time is spent analyzing attacks. They also publish these analyses at regular intervals. One of the most important aspects in these reports is regularly the origin of an IP. This is because certain countries are home to servers that are particularly prone to attacks.
Blacklisting the corresponding IPs therefore makes perfect sense. Especially if the region is not relevant to your target group. This way you can effectively fight back attacks before they reach your website.
You can either create such blacklists yourself by implementing them at the server level, or you can use a security plugin with a corresponding function.
Deprecated WordPress
WordPress is a modular system. It consists of the core, i.e. the core software, the plugins and the themes. One of the biggest dangers for WordPress installations comes from the fact that many WordPress websites do not get regular updates.
This has the most different reasons. These range from incompatibilities at Plugins and Themes, to ignorance or lack of time for an update.
Where delayed core updates can lead to, was impressively shown in February 2017: a security vulnerability in WordPress version 4.7.1 became known, and there was a call to update to version 4.7.2 as soon as possible.
Within a very short time, the news provoked mass attacks on WordPress websites (because the gap was not yet known before the official announcement). Again, the manufacturers of the corresponding security software provide figures: within just a few days, a total of one and a half to two million websites had been hacked. Previously, an employee of Wordfence had discovered the vulnerability.
If you remember that currently more than 43 percent of the entire Internet is WordPress-based, you can get a pretty good idea of what could happen should such a breach go unnoticed. It is therefore advisable to automate or have automated the updates of the WordPress core.
By the way, this mainly applies to the so-called minor updates, i.e. version numbers with three digits, e.g. 4.7.4. These are the so-called "security and maintenance releases" and should always be installed as soon as possible. For larger version jumps, e.g. from 4.7 to 4.8, the situation is somewhat different: Here, the focus of the updates is on functions and general improvements.
Obsolete Plugins and Themes
What applies to the WordPress core, of course, also applies to the plugins and themes: Outdated plugin versions almost always harbor security vulnerabilities - and avoidable ones at that.
According to a security study on content management systems, the German Federal Office for Information Security (BSI) has a similar view. The BSI data refers to the period from 2010 to 2012. 80 percent of the officially reported vulnerabilities could be traced back to extensions - i.e. in most cases to Plugins.
A search for exploits using ExploitsDatabase returned over 250 exploits for WordPress . The majority of exploits for WordPress Plugins have been entered here.
- BSI (2013): "Security Study Content Management Systems (CMS)".
In practice, plugins are a favorite point of attack. And with more than 50,000 extensions in the official plugin directory of WordPress also a very productive one. The starting point for such attacks are then gaps in the code of the plugins.
Here it is important to understand: Such gaps will always exist. There is no such thing as a 100 percent secure system. And: A lack of updates at plugin or theme does not automatically mean that it is insecure. Even if the update frequency is a good indicator for the support quality of a manufacturer. However, it could just as well be that no security vulnerabilities have been discovered so far.
But if any are discovered, the plugin provider will (hopefully) also provide an update that closes the gap. If they don't, attacks like SQL injections or cross site scripting (XSS) are possible. The former involves manipulating your website's database. In this way, new admin accounts can be created and your website can be infected with malicious code or turned into a spam spinner.
XSS attacks are basically about placing JavaScript on your website. Among other things, this can be used to inject forms into your website that steal users' data. Completely unobtrusive, encrypted with SSL and in a trusted environment.
And because Plugins and Themes offer so many points of attack, you should always pay attention to the number of Plugins and make sure not to leave them in a deactivated state, but really uninstall them when you don't need them anymore.
shared hosting
These disadvantages are already inherent in WordPress. But of course, since your website has to come online somehow, WordPress hosting is also an important security aspect. Since the security of WordPress and WordPress hosting is a very complex and multifaceted topic, I would like to talk here first only on the big disadvantage of shared hosting. Again, this doesn't mean that I want to talk you out of shared hosting. It makes a lot of sense, especially from a price point of view. But shared hosting comes with a decisive disadvantage that you should be aware of.
With shared hosting, several websites are located on one and the same server. The websites also share the IP address. This means that the state and behavior of one website can also negatively affect all other websites on the server. This effect is called the Bad Neighbor Effect and refers to spamming, for example. If a website on your server causes the IP to be blacklisted, this can also affect your offer.
In addition, it can lead to an overuse of resources, for example, if one of the websites on the server is caught in a DDoS attack or is affected by a massive attack. Thus, the stability of your own service is to a certain extent always dependent on the security of the other websites on your server.
For professionally operated WordPress websites, a virtual or dedicated server makes sense. Of course, the security concepts of hosters also include backup solutions, firewalls and malware scanners, but we will discuss these in detail elsewhere.
Conclusion
WordPress is insecure. And that is because of its modular structure. Its greatest strength can thus become its greatest weakness. The good news is that you can easily work around this inherent weakness. More than the effort in account management and password creation and updates is basically not needed.
Of course, these measures do not turn your website into Fort Knox. But they are the cornerstone of your security concept. If you don't take them into account, they can undermine all other security measures. And you can influence these aspects on your own. That is why it is so important that you are always aware of them.
