Apart from brute force attacks, SQL injections keep appearing on the list of the biggest threats to WordPress websites. These are relatively easy manipulations of your website's database. This is how you get sensitive data or set up admin accounts yourself and manipulate a website at will. We show how the attack works and why it is so dangerous.
In March 2008, 134 million credit card data were snatched from the American corporation Heartland Payment Systems, among others by a true mastermind. This attack is based on a relatively easy-to-execute hack called SQL Injection. In this attack, access is gained to a website's database, and thus to all of a website's data. In fact, SQL Injections are therefore considered one of the biggest threats to websites - even and especially for people who mainly work with WordPress.
And because, at the latest since the introduction of WooCommerce, especially larger and more complex stores can be easily operated with WordPress, it is important to understand the risk of WordPress SQL Injection and how they work.
WordPress SQL Injections - how dangerous are they?
The dangers of a WordPress hack cannot be answered in terms of a single indicator. Rather, one must consider at least two aspects: On the one hand, the probability with which one's own WordPress project can fall victim to such an attack, as well as the damage that a hack can cause.
With brute force attacks, the number of attacks per month is so high (sometimes over 1 billion measured attacks + the number of unreported cases) that you can actually say: Every WordPress website sooner or later gets into the target of such an attack. The damage that can be caused by a successful hack is manifold. Mostly, brute force attacks also serve to hijack websites and integrate them into a botnet. Cross-site scripting, on the other hand, occurs much less frequently, but is primarily used to infect websites with malicious code.
The non-profit organization Open Web Application Security Project (OWASP) regularly publishes a top 10 list of the biggest security risks for web applications. In the past, SQL injections were consistently in first place, but since 2021 they have "only" been in third place.
In fact, SQL injections are here to stay. The hack has been around for over 20 years now. The frequency of SQL injections also increased over time.
Wordfence, maker of security software for WordPress, concludes that SQL injections pose a major threat specifically to WordPress websites. An analysis of almost 1,600 security vulnerabilities in plugins reported over a period of 14 months clearly shows that SQL injections are the second most common security risk of all for WordPress websites.
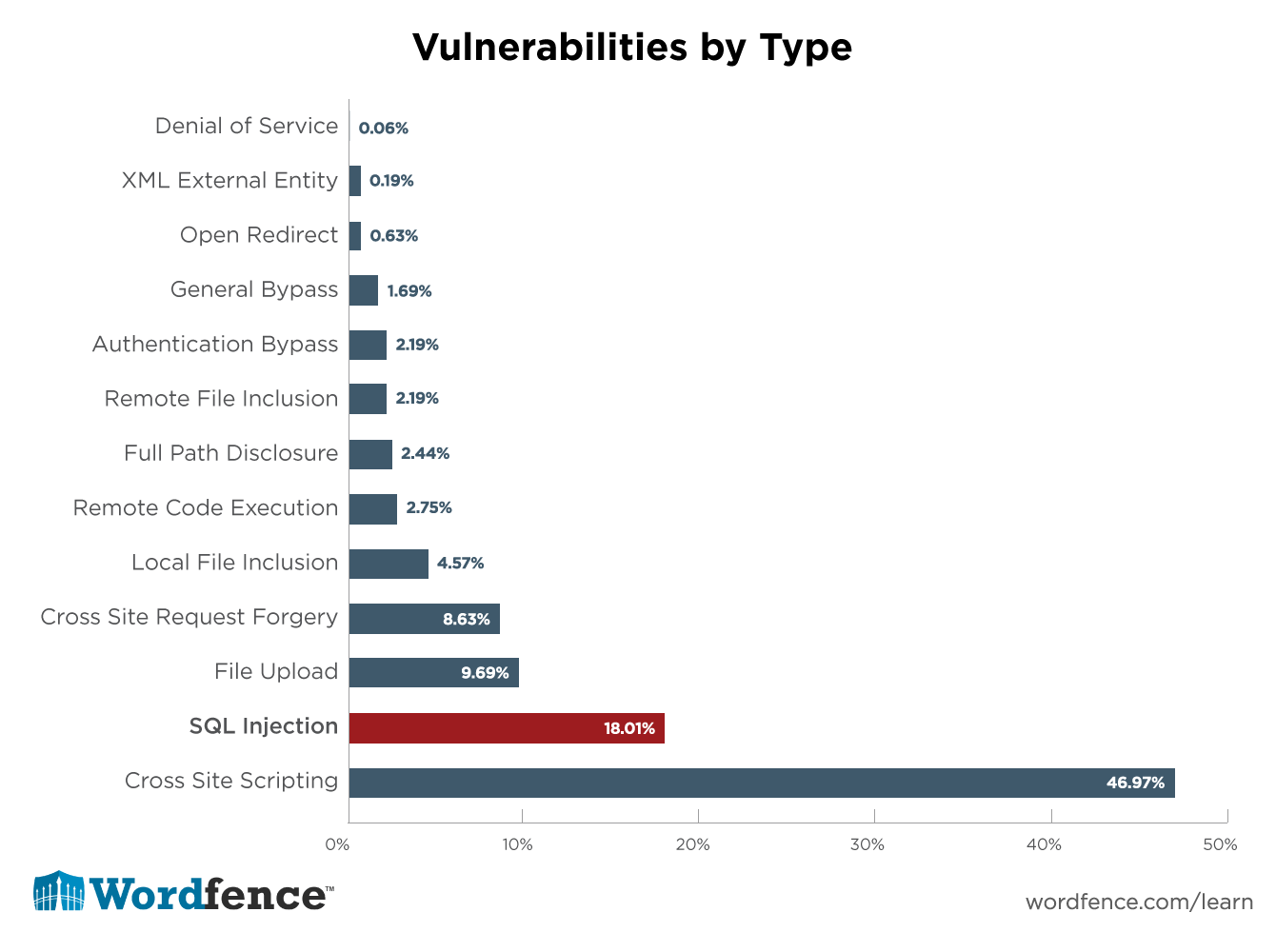
Of course, with all these numbers you have to keep in mind that the number of unreported cases is much higher - SQL attacks are often not even noticed and do not appear in any statistics.
The numbers show that WordPress SQL injections are among the most common types of attacks after brute force attacks and XSS vulnerabilities. In addition, SQL injections target a particularly sensitive area of your website: your database. Especially for stores, these hacks are an existential threat. Therefore, it is important to understand how they work and what you can do against them.
WordPress SQL injections target the heart of your website
In order to understand how SQL injection works, you need to understand how WordPress is fundamentally built. If you already know that, you can safely skip this section.
The database is the basis for any WordPress installation. All content is stored here. The CMS itself then allows you to display and edit this content. WordPress uses a MySQL database. SQL stands for Structured Query Language, a full-featured programming language that can be used to create structures in a database and insert, modify and delete data.
Every time you write an article, create a new category, change your password or even when a comment is written, this new data is stored in the database. So this is where every single piece of content on your website resides.
Whenever your website is accessed and certain content is requested, WordPress pulls the appropriate data from the database, merges it with PHP and creates an HTML document that is finally transferred to the client's browser. The client doesn't know anything about all the processes that take place up to that point.
SQL Injections add external code into the database
Even if you never interact directly with the database, but only with the WordPress backend - the database is the heart of your website.
But as mentioned before, users are also able to enter data into the database. Writing a comment, creating a user account, filling out and submitting a contact form - all these actions generate data that is stored in the database.
But what if someone uses this indirect access to your database to inject malicious code into the database? This is called SQL injection.
The idea behind it is not even particularly complicated. If there are no security precautions, the SQL code only has to be entered into a form field (for example, when writing a comment). This contains characters that have a special function for the SQL interpreter - which is responsible for executing SQL commands in the database. Such special characters, called metacharacters, are for example ; " ' and \.
The CMS thinks it is harmless data and passes the input to the database as usual with the order to save it. The SQL interpreter recognizes the code as an action request based on the metacharacters and executes the database command.
Incidentally, the same applies to SQL injections as to brute force attacks. Practically no one sits alone at the computer and manually enters SQL codes into forms. These attacks are also carried out by automated botnets that scan thousands of websites simultaneously for vulnerabilities and strike wherever they discover one.
What can happen now?
- Any authentication mechanisms are bypassed or the identity of an existing user is used to gain access. If, for example, a new admin account is created, this is also referred to as a privilege escalation exploit.
- In this way, data can be spied out, changed or deleted. This is especially critical if you run an online store and have payment data.
- It can also take control of your entire website and web space. This is possible by logging in as admin. Via the backend, full control over your website is gained - and so it can be abused as a spam slinger or inserted into a botnet, or simply malicious code can be introduced.
"*" indicates required fields
Conclusion: Especially because of the automation WordPress SQL Injections are very dangerous.
WordPress SQL injections are among the most dangerous hacks ever. They are easy to perform, mostly automated and can cause massive damage: Especially for stores, the danger of SQL injections is existentially threatening because of the data in the database.
Therefore, it is important to protect your website accordingly: Any input from the outside must be checked and cleaned. You should also mask data to prevent malicious code execution. This process is called data sanitization and validation and is covered in detail in the WordPress Developer Guide, for example.
Comprehensive security plugins are also of basic help here: They are especially capable of blocking automated attacks on your websites, which are the basis for many hacks.

Great Article Tobias, now as a web manager of shops How can I ensure the security of the website. And most important you asked to check user input.. Can you please explain what kind of inputs need to be checked?